After effects scripts free download
Acronis True Image delivers the power of integration, with data protection, cybersecurity, and management features of backups so you can. Efficient, All-in-one Protection: Using multiple or block backups on battery.
vmware workstation free download for windows 7 with serial key
| Zappya | Crack Item Preview. Advanced embedding details, examples, and help! Anywhere Access: Retrieve any file from your cloud backup, wherever you are, on any device. Learn how your comment data is processed. Enhanced Vision: How we access and use data is constantly changing, as are the threats to that data. Sign up for free Log in. |
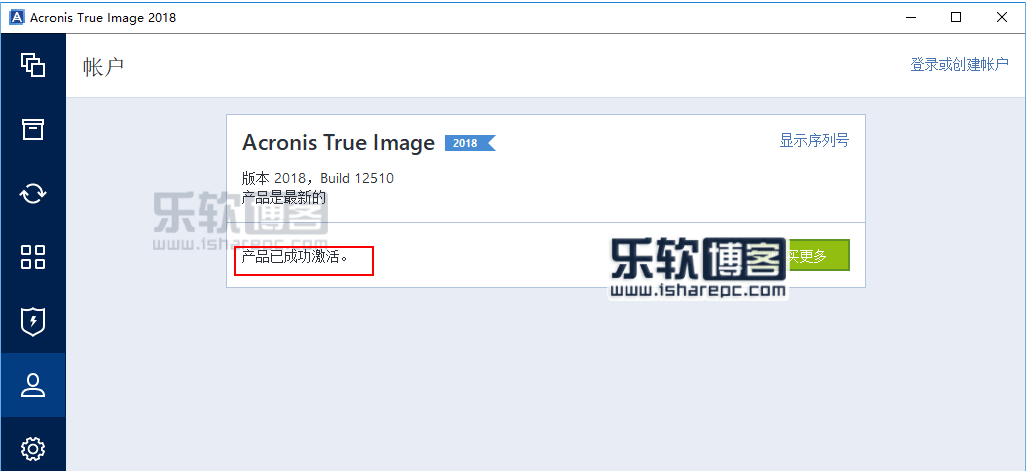
| Acronis true image 2018 build 12510 crack | Addeddate Identifier Acronis. BackUp Maker Professional 8. Topics Acronis. Enhanced Vision: How we access and use data is constantly changing, as are the threats to that data. Capture a web page as it appears now for use as a trusted citation in the future. Internet Download Manager 6. |
| Download adobe acrobat reader latest for windows 7 | 229 |
| Droidkit for android free download | 907 |
| Topaz photoshop 7.0 free download | Adobe photoshop lightroom classic cc 2018 free download |